Proofpoint Enterprise
Organization-wide cybersecurity management at your fingertips.
Beyond Email Protection
Proofpoint Enterprise encompasses multiple facets of security to protect an organization from the latest email-based attacks and enable administrators to easily monitor email and data security practices across the organization.
Advanced Protection
Proofpoint's Targeted Attack Protection includes deep content analysis, signature-based virus and malware scanning, and granular filtering controls.
Comprehensive Management
Proofpoint excels at providing administrators with tools for accelerated threat response and monitoring for email, data, social media, mobile apps, and your remote workforce.
Complete Solution
Fully integrated Email Continuity, Archiving, and Encryption are also available to protect business continuity and ensure compliance regulations are met.
Proofpoint Certified Engineers
Leverage our Proofpoint Enterprise expertise to create your ideal security posture. Proofpoint certified engineering is included for your deployment.
Security Awareness Training
Protection starts with people. Empower your people and transform users into defenders who report.
Combat Data Loss and Insider Risk
Gain visibility and contextual insights, mitigate external and internal data risk, and streamline your incident response.
Comprehensive Advanced Protection
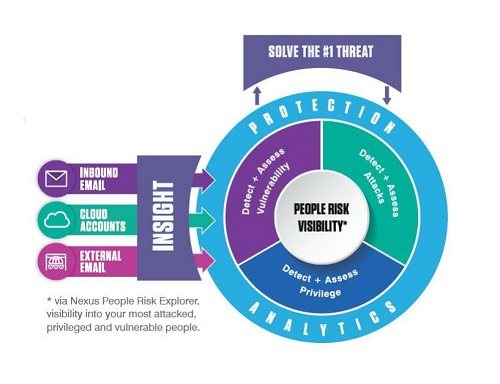
Image by Proofpoint
Protect the #1 Threat Vector: Email
94% of threats begin with email.
Questions to consider:
- Do you know who's being attacked and what threats are targeting them?
- How concerned are you about Business Email Compromise / imposter attacks?
- What about phishing and ransomware attacks?
- What would happen if an email threat passed through your current solution to a user?
- What does your security team typically do when phishing, BEC, or compromised accounts happen?
- How much time does your staff spend detecting and responding to these threats?
Proofpoint's industry leading Enterprise Email Security solutions stop email threats including: malicious attachments/URLs and non-malware threats, such as phishing and business email compromise (BEC). Customers get visibility into who are their most attacked people and how they're being attacked - providing actionable insight to speed up time to detect, remediate, and reduce breach risk.
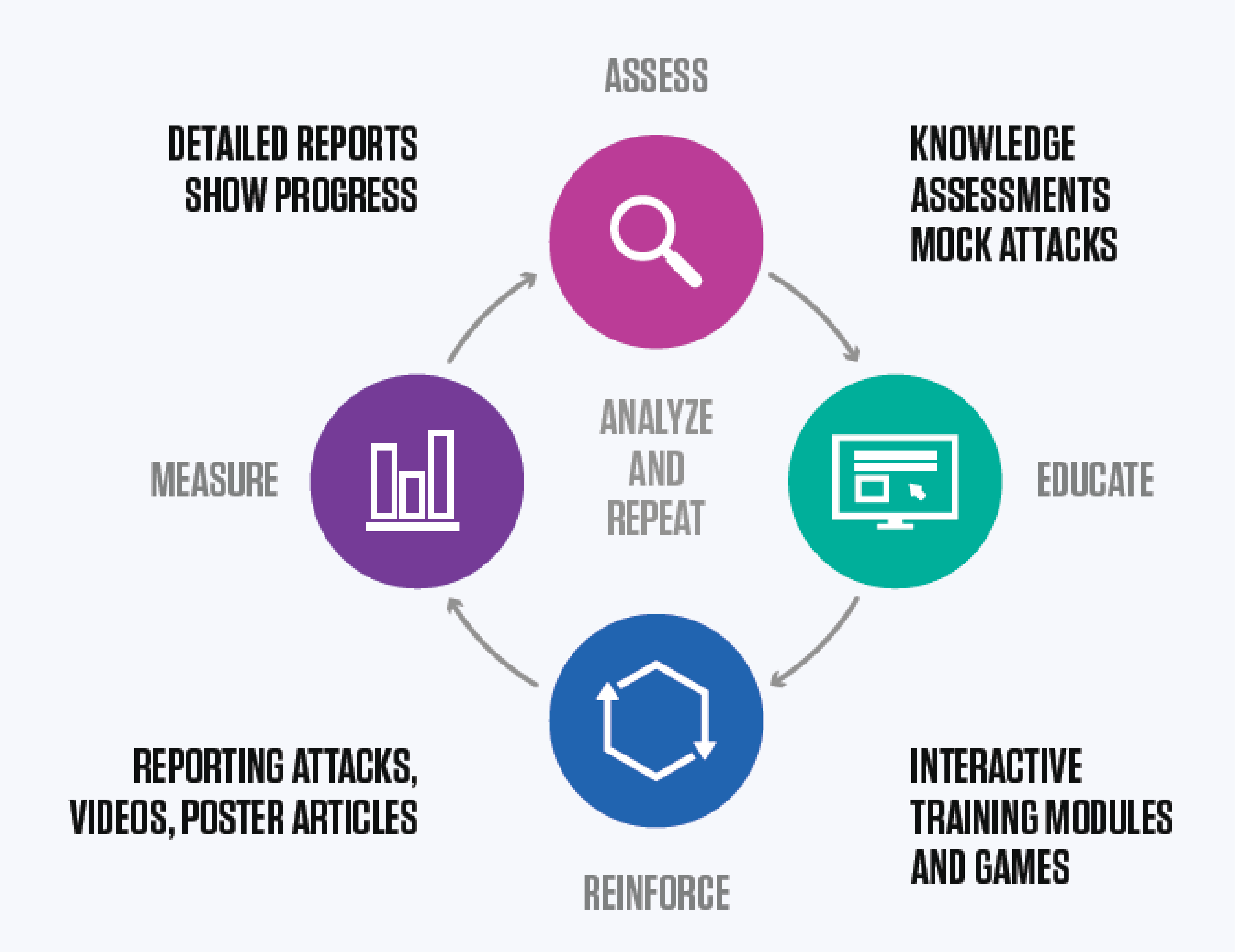
Security Awareness Training
Almost all cybersecurity attacks are aimed at people.
Questions to consider:
- In your organization, what percentage of attacks are the result of successful spear phishing?
- How are you educating your users about cybersecurity threats?
- How are you measuring success with your security education program?
- How often are you training end users?
- Are you able to customize your training content?
- Can you provide relevant content based on the most recent threats?
Teach your employees secure behavior with Proofpoint Phishing Simulation and Security Awareness Training. This cloud-based training reduces successful phishing attacks and malware infections by up to 90%.
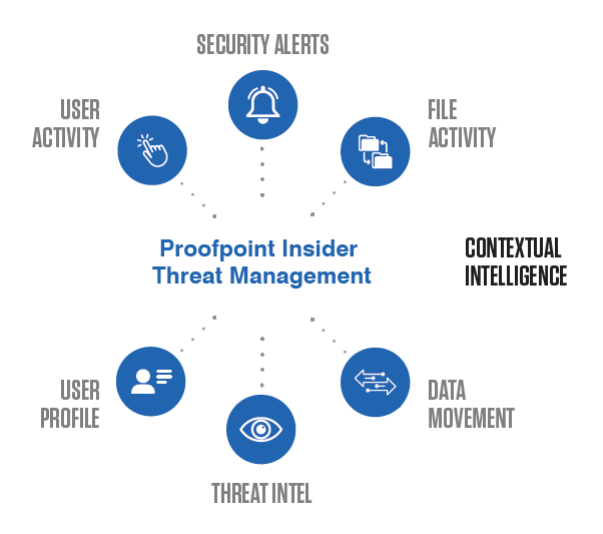
Stop Data Loss with Insider Threat Management
50% of data breaches involve an insider.
Questions to consider:
- How do you know where all your sensitive assets are, the users who have access to them, and how those users interact with those assets?
- On your list of importance, where do you rank visibility into high-risk users, such as privileged users and/or third-party contractors?
- How are you correlating your logs and alerts to user files, endpoints, email, and web?
- With the rise of remote workers and third-party contractors, how do you fill the gaps into visibility across sensitive file movement, websites/apps usage, and critical systems access by trusted insiders?
Traditional ways of protecting data and intellectual property are easy to bypass and complex to implement and maintain. The Proofpoint Enterprise Insider Threat Management platform empowers security teams to detect insider threats, streamline investigations, and stop data exfiltration.
Benefits of Proofpoint Enterprise
Protect your organization with the most advanced cybersecurity platform on the market.
Advanced Threat Analysis
Proofpoint's patented MLX technology provides dynamic protection against emerging email threats, including viruses, malware, imposter emails, spam, graymail, and more. The Proofpoint filtering algorithms are highly accurate with an extremely low rate of false positives. Targeted Attack Protection evaluates URLs and attachments for threats that could be missed by more traditional signature or reputation-based analysis.
Users are protected no matter where or from which device they access email. Your customized policies are applied to all inbound and outbound emails, making it easy to manage messaging across multiple servers and locations.
Accelerated Response Time
Proofpoint Enterprise gives administrators the tools they need to manage organization-wide email activity and quickly respond to potential threats. Real-time notifications provide details of attacks or suspicious behavior, including specific users that may be affected. Advanced message-tracing features make it easy to pinpoint log data based on dozens of search criteria.
Custom policies can be created to further fine-tune message management, including re-routing email delivery based on specified criteria. Quarantined messages can be segmented into different folders with varying permissions depending on the type of threat. In addition, Smart Send and other user features enable employees to resolve errors on their own, thereby freeing up IT resources.
Reduce Risk and Liability
Proofpoint offers a suite of services to safeguard your business reputation, ensure continuity of service, and enforce compliance policies. Email Continuity provides secondary email service for both on-premise and cloud services with automatic failover and restoration. This add-on allows network administrators to focus on restoring the primary email service while employees can continue to send and receive emails from any device or location via the web portal or Outlook integration.
Proofpoint outbound filtering helps prevent data loss and safeguards critical information from email compromise or compliance violations. Choose from dozens of pre-configured policies or create your own to automatically detect, block, or re-route potentially compromising messages. Policy-based encryption and disclaimers can be applied to outbound messages.
Add Proofpoint Archiving to have a fully searchable history of organization-wide email communications. Archiving is essential for compliance with many regulatory policies and simplifies data access for audits and litigation. Data is encrypted from site to site with DoubleBlind key architecture, no onsite hardware is needed, and storage space is unlimited.
Privacy and Reliability
Proofpoint Enterprise is configured as a private cloud hosted in regional data centers with no on-site hardware required. Most SaaS email security solutions are hosted in a public cloud. However, Proofpoint Enterprise is deployed within a private cloud configuration used only by your network. Data centers within your company's geographical region are utilized to minimize latency.
Proofpoint is compatible with most email services, including Exchange, Lotus Domino, Zimbra, Office 365, G Suite (Google Apps), and more. There is no need to purchase new equipment or alter your existing network infrastructure.
Proofpoint Enterprise Features
MX Record Protection
The Proofpoint Enterprise records will replace your existing MX records. This DNS configuration ensures that all messages pass through the email security system. In addition, it makes it more difficult for spammers to directly target your company mail server and offers protection against denial of service (DoS) and directory harvest attacks (DHA).
Inbound/Outbound Protection
All inbound and outbound messages are scanned for viruses, malware, and suspicious content or behavior, including phishing attempts. The Proofpoint SLA guarantees 100% protection against viruses along with 99% of spam blocked on inbound messages, and no more than 1 false positive for every 350,000 emails.
MLX Technology
Proofpoint uses deep content analysis, signature-based virus and malware scanning, and granular filtering controls to safeguard your network from emerging email threats.
Email Firewall
Set rules for inbound emails based on multiple conditions along with specified routes and actions.
Reputation Controls
An administrator can manage Reputation Service settings or add senders/recipients to the organization-wide safe-block lists based on email address, domain, hostname, or IP.
Spam and Virus Policies
Spam and virus settings can be modified at a granular level for different types of emails, such as malware, phishing, adult spam, bulk, etc. Custom policies can also be created.
Customizable Email Quarantine
Different types of suspect emails are diverted to corresponding folders in the message quarantine. Permissions, retention, and actions can be varied depending on the folder content.
Compliance and DLP
Proofpoint includes multiple options to aid in compliance with HIPAA and other legal standards. These features include disclaimers, policy-based email encryption, groups, and message routing.
Data Discover Add-on
Install this tool on data storage systems to identify sensitive data and apply policies to data in transfer or at rest.
Mobile Defense Add-on
Monitor Android and iOS devices for risky app behavior or permissions. Create automated workflows to notify users and admins, block access to compromised devices, and restore access when the appropriate action has been taken.
Social Media Protection Add-on
Monitor your presence across all major social media platforms to indentify unauthorized accounts, enforce compliance and conduct standards, delete posts/comments with phishing or malware, provide authorized users with a single sign-on, and more. All features are managed from an easy-to-access dashboard.
Private Cloud
Proofpoint Enterprise is deployed in a private cloud configuration across at least two locations. The uptime SLA is 99.999%.
Regional Data Centers
Your emails will be processed through facilities in the same region as your primary business location. This configuration helps minimize latency for faster processing speeds.
MX Backup
Mulitple delivery routes can be configured in Proofpoint to allow for failover. In the event that all delivery routes are unavailable, Proofpoint will hold incoming messages for up to four days. All held messages will be delivered when the destination server becomes available.
Email Continuity Add-on
Access is available via the web portal or Outlook integration. A 30-day archive of email history is available to users (Proofpoint Archive users will have access to their full email history).
Data Security
Proofpoint Archiving encrypts all stored messages from site-to-site and at rest with DoubleBlind keys.
Fast Search Guarantee
Proofpoint's SLA includes a 20-second search guarantee even with a complex search of the full archive. The average search time is 6 to 7 seconds.
No Storage Limits
Archiving is priced on a per user basis without storage or retention restrictions. Data ingestion options mean you can import your company's full email history.
Outbound Journaling
Enable email journaling on your mail server to have a copy of all outbound messages saved to the archive.
Audits and Reports
A full policy history is maintained and reports can be easily exported in industry-standard formats to streamline compliance.
Administrative Access
Administrators and end-users can manage all Proofpoint services made available to them through a single web-based interface.
User Creation
Configure Proofpoint to automatically add users and groups based on your LDAP organization. Alternately an administrator may import users via .csv file or manually create users and groups.
User Permissions
Proofpoint allows an administrator to manage user authentication profiles, application settings, access, and sessions. Administrator roles can be created to give some users special privileges.
Logs and Reports
Proofpoint includes many pre-configured report templates which can be customized by time period, route, and frequency.
Alerts
Create multiple alert profiles for different recipients. Add customized rules including condition, action, and frequency.
Languages
Users can select their language of choice with 37 options available